REcon 2026 Speakers
Conference Dates: June 19-21, 2026
Location: Hilton DoubleTree Montreal
Speakers Announced Soon
We are currently reviewing CFP submissions.
Speaker announcements will begin shortly.
Trainers
Our 2026 training instructors include world-class security researchers and practitioners:

Sina Kheirkhah
Advanced .NET Exploitation
Full-time vulnerability researcher specializing in low-level exploitation. Pwn2Own "Master of Pwn" 2025.
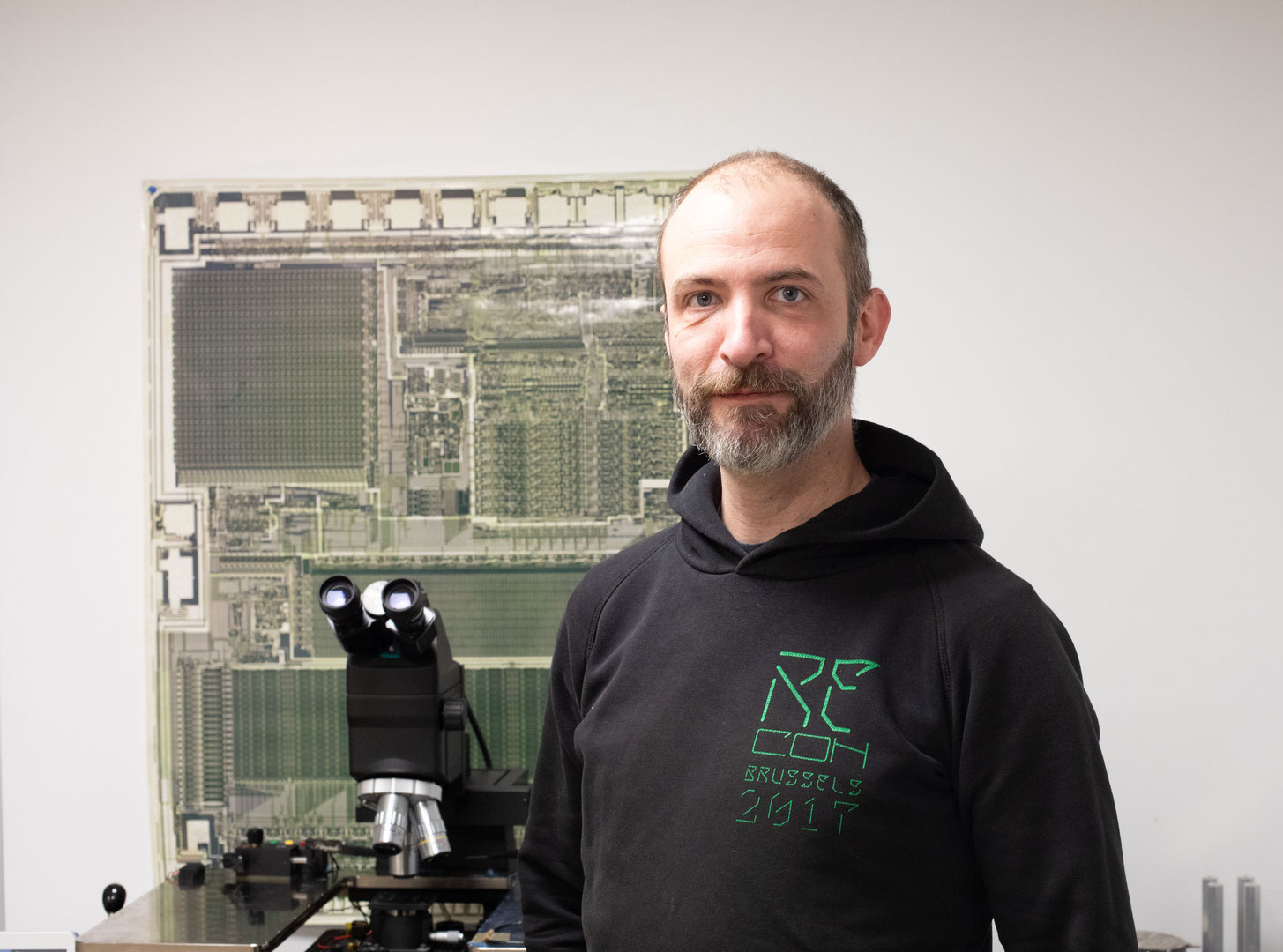
Olivier Thomas
Advanced IC Reverse Engineering & Data Extraction
Expert in integrated circuit reverse engineering and hardware security.

Marion Marschalek
Advanced Malware Reverse Engineering
Renowned malware researcher and reverse engineer.

Richard Johnson
AI Agents for Cybersecurity
Expert in applying AI and machine learning to security research.

Tim Blazytko
Software Deobfuscation Techniques
Co-founder of emproof, expert in code deobfuscation and fuzzing.

Yarden Shafir
Windows Internals for Reverse Engineers
Vulnerability researcher at Vigilant Labs, Windows internals expert.

Andrey Konovalov
Exploiting the Linux Kernel
Linux kernel security researcher and exploit developer.

Cristofaro Mune
The Art of Fault Injection
Co-founder of Raelize, 25+ years in security, expert in hardware attacks.

Niek Timmers
The Art of Fault Injection
Co-founder of Raelize, device security expert specializing in fault injection and secure boot bypass.

Julien Cohen-Scali
Attacking Real World IoT
Cybersecurity Researcher at FuzzingLabs, specializing in IoT and embedded security research.

Lucas Van Haaren
Attacking Real World IoT
Security researcher at FuzzingLabs focused on IoT vulnerability research and embedded systems.

Kyle Martin
Automated Reverse Engineering with Binary Ninja
Cyber security software engineer, leads Binary Ninja trainings and develops advanced analysis tools.

Dr. Malachi Jones
Automating RE with AI/ML
Principal Cybersecurity AI/LLM Researcher at Microsoft, leads research on red team agent autonomy.

Joe Mansour
Automating RE with AI/ML
Security Researcher at Microsoft specializing in reverse engineering malware.

Corentin Bayet
Bug Hunting in Hypervisors
CTO of REverse Tactics, Pwn2Own VM escape expert and hypervisor security researcher.

Bruno Pujos
Bug Hunting in Hypervisors
CEO of REverse Tactics, expert in firmware and UEFI reverse engineering.

John McIntosh
Building Agentic Reverse Engineering Tools
Security researcher at Clearseclabs, Ghidra tooling expert and automation specialist.

Caleb Davis
Embedded and Shredded
Founding member of SolaSec, specialist in embedded hardware security and PCB analysis.

The FLARE Team
FLARE Team Guide to RE Malware
The FLARE team at Google Cloud (Mandiant) is comprised of veteran reverse engineers.

Silvio La Porta
Modern Malware OPSEC
CEO of RETooling, malware reverse engineering expert with extensive threat analysis experience.

Antonio Villani
Modern Malware OPSEC
Co-Founder of RETooling, specializes in threat actor analysis and malware research.

Kai
Modular Implant Design for Windows
PhD at Northeastern University, specializes in implant development and offensive security.

Daniel Frederic
Reversing Modern Binaries
Expert in reverse engineering Rust and Go binaries, malware analysis specialist.

Mathieu Hoste
Reversing Modern Binaries
Security engineer at FuzzingLabs, Rust and blockchain security expert.

Tanguy Duhamel
Rust Development for Cyber Security
Lead Developer at FuzzingLabs, specializes in distributed fuzzing and Rust tooling.

Tristan Ferreira
Rust Development for Cyber Security
Cybersecurity Expert at FuzzingLabs, developer of FuzzForge fuzzing infrastructure.