| UNIX Privilege Escalation Without Exploitation
Theoretical Support for Hypothesis
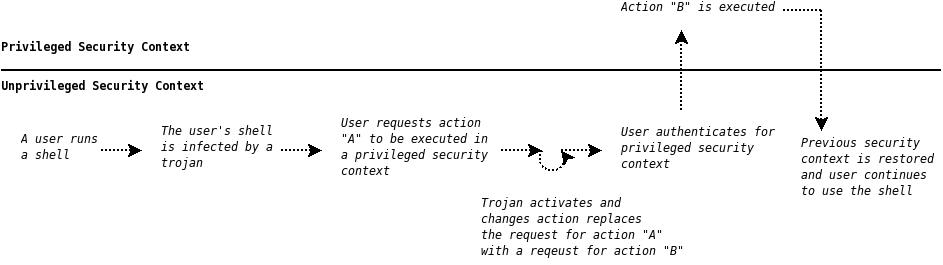
-
In many UNIX systems, the previous security context has full control over what can be executed in the new context. For example, a user wanting to execute ls(1) as root can do so by executing
su -c "ls"
- All applications in the previous context run at same level of privilege. This means that they can be trojaned by any other exploited or infected application in that context
